Welcome to DU!
The truly grassroots left-of-center political community where regular people, not algorithms, drive the discussions and set the standards.
Join the community:
Create a free account
Support DU (and get rid of ads!):
Become a Star Member
Latest Breaking News
Editorials & Other Articles
General Discussion
The DU Lounge
All Forums
Issue Forums
Culture Forums
Alliance Forums
Region Forums
Support Forums
Help & Search
General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsWhiskey Pete's Dirty Desktop -- EmptyWheel
https://www.emptywheel.net/2025/04/25/whiskey-petes-dirty-desktop/'We continue to get more details of Whiskey Pete Hegseth’s abysmal operational security.
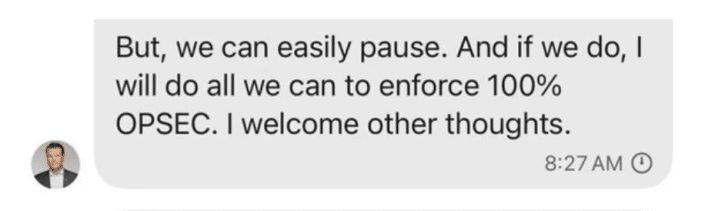
Today, NYT revisited the issue of Pete Hegseth’s shoddy operational security, tracking all the other accounts he had registered under the phone number with which he used Signal.
What they don’t say is the accessibility of his personal phone number could have made it easier to ID the IP address for the computer that (per the AP) Hegseth set up in his office so he could access Signal.
But there’s a detail that remains unexplained, one which makes this more interesting.
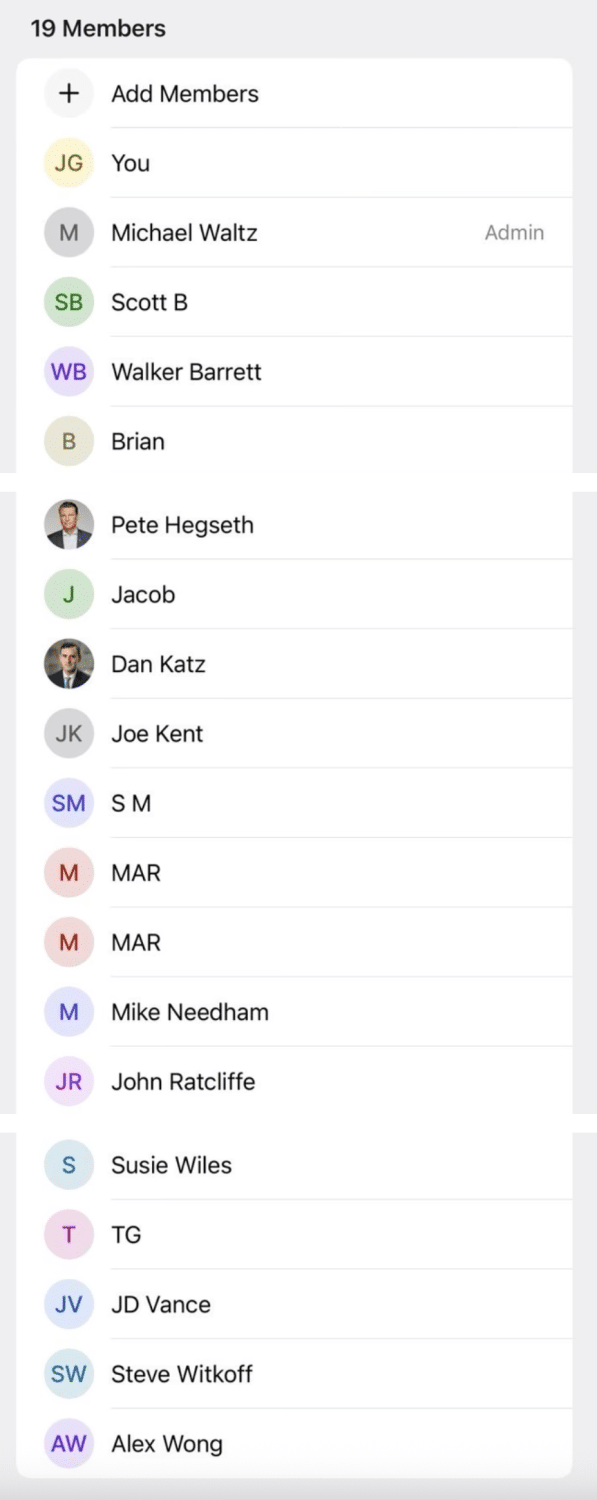
In addition to the texts themselves, Jeffrey Goldberg provided a number of useful details about the Houthi PC small group thread.
He included the list of the 19 people who belonged to it when he left.
. . .
Mr. Hegseth had a significant social media presence, a WhatsApp profile and a Facebook page, which he still has.
On Aug. 15, 2024, he used his personal phone number to join Sleeper.com, a fantasy football and sports betting site, using the username “PeteHegseth.” Less than two weeks later, a phone number associated with his wife, Jennifer, also joined the site. She was included in one of the two Signal chats about the strikes.
Mr. Hegseth also left other digital breadcrumbs, using his phone to register for Airbnb and Microsoft Teams, a video and communications program.
Mr. Hegseth’s number is also linked to an email address that is in turn linked to a Google Maps profile. Mr. Hegseth’s reviews on Google Maps include endorsements of a dentist (“The staff is amazing”), a plumber (“Fast, honest, and quality work”), a mural painter (“Painted 2 beautiful flags for us — spot on”) and other businesses. (Google Maps street view blurs out Mr. Hegseth’s former home.)
What they don’t say is the accessibility of his personal phone number could have made it easier to ID the IP address for the computer that (per the AP) Hegseth set up in his office so he could access Signal.
Defense Secretary Pete Hegseth had an internet connection that bypassed the Pentagon’s security protocols set up in his office to use the Signal messaging app on a personal computer, two people familiar with the line told The Associated Press.
The existence of the unsecured internet connection is the latest revelation about Hegseth’s use of the unclassified app and raises the possibility that sensitive defense information could have been put at risk of potential hacking or surveillance.
Known as a “dirty” internet line by the IT industry, it connects directly to the public internet where the user’s information and the websites accessed do not have the same security filters or protocols that the Pentagon’s secured connections maintain.
Other Pentagon offices have used them, particularly if there’s a need to monitor information or websites that would otherwise be blocked.
But the biggest advantage of using such a line is that the user would not show up as one of the many IP addresses assigned to the Defense Department — essentially the user is masked, according to a senior U.S. official familiar with military network security.
[snip]
Hegseth initially was going to the back area of his office where he could access Wi-Fi to use his devices, one of the people familiar said, and then he requested a line at his desk where he could use his own computer.
That meant at times there were three computers around his desk — a personal computer; another for classified information; and a third for sensitive defense information, both people said.
Because electronic devices are vulnerable to spying, no one is supposed to have them inside the defense secretary’s office. Important offices at the Pentagon have a cabinet or drawer where staff or visitors are required to leave devices.
But there’s a detail that remains unexplained, one which makes this more interesting.
In addition to the texts themselves, Jeffrey Goldberg provided a number of useful details about the Houthi PC small group thread.
He included the list of the 19 people who belonged to it when he left.

. . .
I lived in fear of prison if I did one-tenth of what this idiot did. They are purposefully making any security (OPSEC) meaningless.
1 replies
 = new reply since forum marked as read
Highlight:
NoneDon't highlight anything
5 newestHighlight 5 most recent replies
= new reply since forum marked as read
Highlight:
NoneDon't highlight anything
5 newestHighlight 5 most recent replies
Whiskey Pete's Dirty Desktop -- EmptyWheel (Original Post)
erronis
Saturday
OP
underpants
(190,133 posts)1. Fish bowl
If you work in the public sector, you work in a fish bowl. Everything is open to the public. It’s their business.